Moray - Red Team Tool
Moray (C2 Reverse Shell)
Infiltrate, Exfiltrate, Aggravate.
Project Overview
Simple and fast reverse shell written in GoLang with the sole objective of annoying/gas-lighting the blue team.
Project Goal
My main goal for this project is to be the biggest pain in the ass as possible, without the blue team realizing I am behind their frustrations. This can be achieved by executing payloads that emulate user errors. These can be things such as
- Press the Space key twice when it is pressed once.
- Press the semicolon key when surrounding keys are pressed
- Move the mouse to a random position on the screen
- Periodically toggle caps-lock
- Play Discord notification sounds
- Swap the N and M keys periodically.
- Press the back space twice when it is pressed once
- Randomly click
- Randomly clear Clipboard
It Still Has Power
Despite having a ton of dumb aggravating features, the program can also do normal malware things such as
- Run command using command prompt or bash shell
- Download files from the internet
- Transfer files to attacker machine
- Encoded communication channel
A Deep Dive Into The Tool
Though I do not plan on releasing any source code, I will dive deeper into what the bot does, how it accomplishes its goals, and some insight into the development process. Some things I will not discuss are: How I plan on hiding the malware on an infected machine, or details regarding the final encoding scheme used for sending messages over the network.
Language Choice
For this project, I chose to write all my code in GoLang. There are many aspects of Go that makes it an amazing choice for malware development, but the main factors that drove my decision are
- Low level performance.
- High level syntax
- Compiles to an Exe or Binary easily
- Easy cross platform development
- Super simple concurrency
GoLang is super quick. Though speed is not typically the main focus of a reverse shell, it definitely doesn’t hurt. The language also has support for low level memory management (to an extent) which is great for creating my own screwy encoding schemes, and pointer bull-fuckery. Programming concurrency in Go using Go-routines is also super simple, so using Go will save me a lot of time and pain when creating threaded processes.
The cherry on top of all of this, is that Go cross compiles across multiple OS’s and also has high level syntax. That means I only need to write one application to infect Linux, Mac, or windows machines… and those applications will be easy to write. Of course, hiding the malware will have a different method for each OS, but the meat of the malware is cross platform out of the box.
How it Works
Networking
This program is a C2 (command and control) reverse shell interpreter. In short, Infection starts when a program is installed on the target machine. Once this program is executed, it makes a connection to the attackers server. The attackers server then sends commands to the infected machine, and the infected machine then performs an action based on the command. There are some special things that this this application does regarding the connection, such as:
- If connection to the attacker server is lost or interrupted, The infected application will wait a random interval of time then attempt to reconnect. This adds a extra layer of obscurity to the connection pattern when analyzing traffic.
- The Attacker’s server can send a command to all target devices at once
- All traffic over the network is encrypted using a custom encryption protocol I wrote. If your interested in learning more about this protocol, you can read more about it on my Github: https://github.com/F1shh-sec/String-Encoder
Messages Over the Network
When sending messages over the network, everything is encrypted using a custom encryption protocol. After being encrypted, messages are then Base64 encoded. Encoding the encrypted content allows me to send everything from files to text over the network without worrying about whitespace or new line characters breaking my buffer.
Features
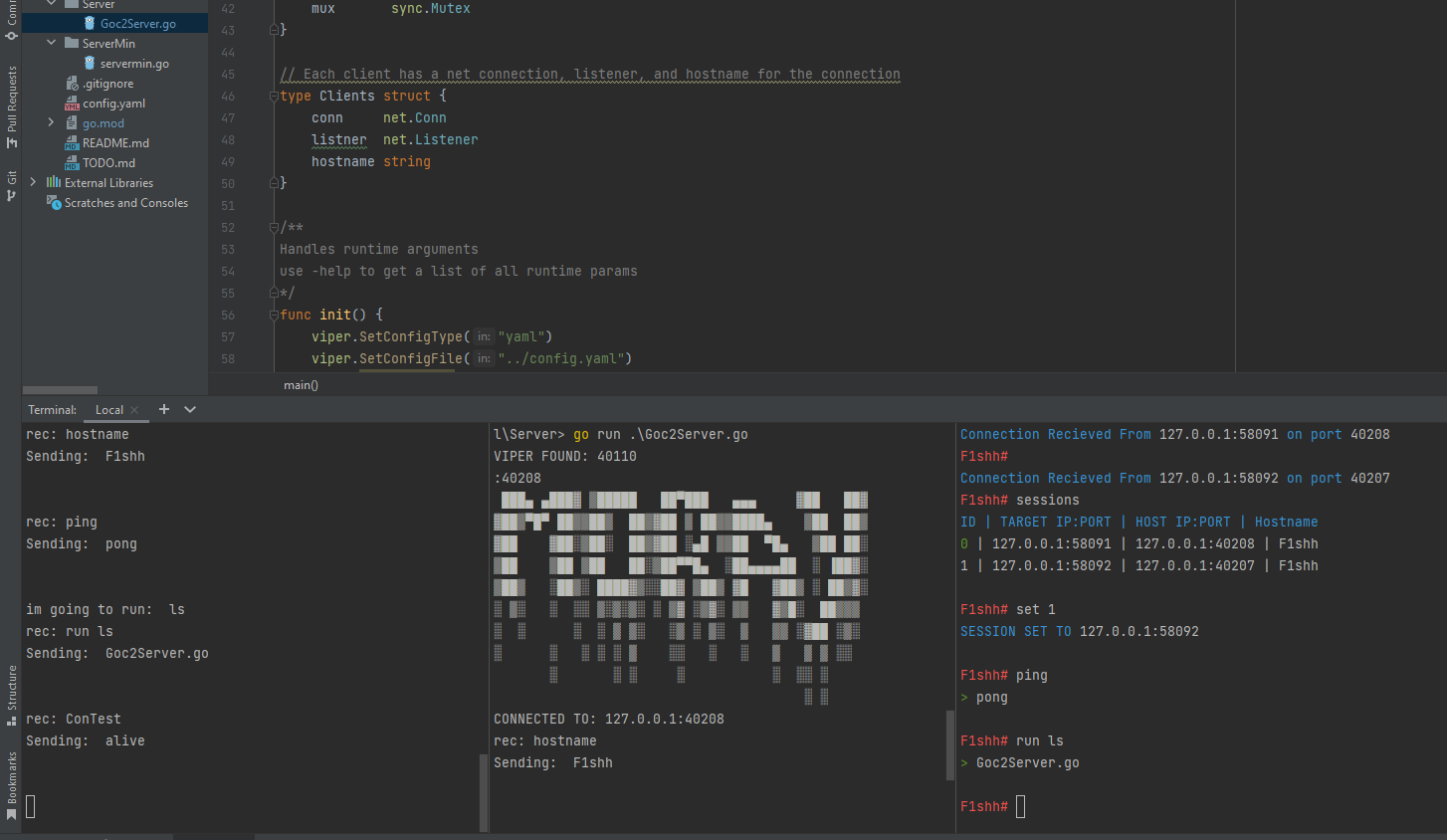
- Multi handler allows for dynamic port assignment or infected machines and easy management of multiple clients from a single attacker terminal. Includes functions to check connections, view sessions, and swap sessions. Were cruising in C2 baby.
- Automatic reconnection of infected machines after network interruptions (good for competitions where network connection may be unreliable). Implemented random time intervals between connection attempts to better hide the connection.
- Custom encryption protocol for all client server communications.
- Mass file discovery to easily locate documents
- Ability to exfiltrate files off of the infected machine
- Ability to download files to a target machine
- Full reverse shell capabilities (converted tool from a bind shell to a reverse shell)
- Cross platform: works on both Linux and windows (not tested on MacOS)
- Control user input:
- Click mouse buttons
- Press keys
- Scroll wheel n times
- Teleport mouse to random locations
What I’m Working On
- General optimizations and stability.
- Beautifying attacker interface (constancy in terminal coloring)
- Settings configuration from a external file
- More interpreter commands
- Better persistence and obfuscation
Want to Get Involved?
Too bad.
I currently have no plans to make this software open or public because I don’t want to contribute to the amount of malware floating around in the wild. This tool is only intended for use in Cyber security competitions.